Confirmation of particle's existence leads to award for work published in 1964.
by John Timmer
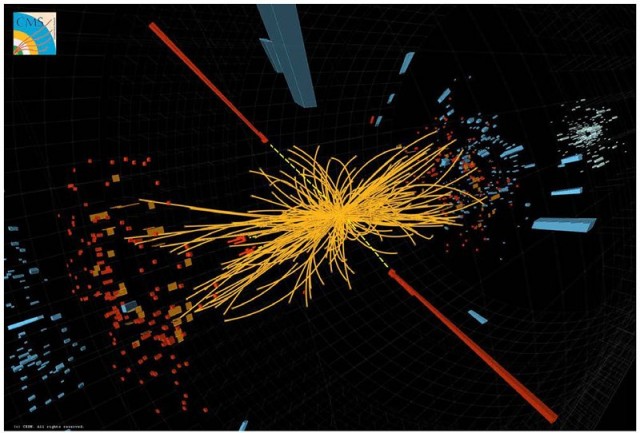
A collision in the LHC's CMS detector.
Last year, after decades of waiting, a handful of theorists had their work confirmed with the announcement that scientists had discovered an elusive particle called the Higgs boson. Now, just over a year later, two of those theoreticians are being awarded the Nobel Prize in physics.
The Higgs boson is a manifestation of the Higgs field, an invisible entity that pervades the Universe. Interactions between the Higgs field and particles help provide particles with mass, with particles that interact more strongly having larger masses. But despite its central role in the function of the Universe, the road to the papers that predicted the existence of the Higgs was bumpy, as was the process of discovering it.
The idea of the Higgs was a consequence of studies on the weak force, which controls the decay of radioactive elements. The weak force only operates at very short distances, which suggests that the particles that mediate it (the W and Z bosons) are likely to be massive. While it was possible to use existing models of physics to explain some of their properties, these predictions had an awkward feature: just like another force-carrying particle, the photon, the resulting W and Z bosons were massless.
Over time, theoreticians managed to craft models that included massive W and Z bosons, but they invariably came with a hitch: a massless partner, which would imply a longer-range force. In 1964, however, a series of papers was published in rapid succession that described a way to get rid of this problematic particle. If a certain symmetry in the models was broken, the massless partner would go away, leaving only a massive one. The first of these papers, by François Englert and Robert Brout, proposed the new model in terms of quantum field theory; the second, by Peter Higgs, noted that a single quantum of the field would be detectable as a particle.
Robert Brout died in 2011, so Englert (currently at the Free University of Brussels) was honored for his contributions, as was Higgs, who is at the University of Edinburgh. The third paper, by Gerald Guralnik, Carl Richard Hagen, and Tom Kibble, was not recognized by this award, possibly due to the prize's stipulation that only three people be recognized. (For the same reason, none of the people who spotted the Higgs at the LHC are recognized; as the Nobel documents point out, each of the two detectors credited with the discovery had a staff of over 3,000 researchers.)
But the third paper provided an independent validation of the general approach, as did a completely independent derivation by students in the Soviet Union. By 1967, Steve Weinberg had extended the Higgs mechanism to account for the mass of electrons and heavier leptons, and in 1971, Gerhard ‘t Hooft and Martinus Veltman figured out how to get rid of a few annoying infinities in some of the equations. By 1983, the W and Z bosons had had their masses determined, providing an experimental validation of some of the predictions made by the theoreticians.
But while the Higgs field managed to get a lot of things in the Standard Model to work properly, we still didn't have experimental validation of one of its predictions: the Higgs particle. Precision measurements of the masses of some of the heavier particles put an upper limit on the Higgs mass at about 150GeV, while experiments with the Large Electron-Positron collider (the LHC's predecessor, built in the same tunnel) eliminated everything under 115GeV. Meanwhile, years of running the Tevatron had produced a weak signal of around 120GeV, one that was just over two standard deviations above background noise.
That was where things stood when the LHC started up. Within a few years of operation, the new collider had generated enough data to detect a five-sigma signal at just above 125GeV, enough to announce discovery. On the day of the announcement, Englert and Higgs were in the audience at CERN. Now, they will have a chance to meet again with a different kind of audience—one with the King of Sweden.