"Quantum cookie" attacks are plausible but only in highly limited cases.
by Dan Goodin

by Dan Goodin

An image taken from documents former NSA contractor Edward Snowden provided to The Guardian newspaper.
One of the more intriguing revelations in the most recent leak of NSA documents is the prospect that the spy agency is using browser cookies from the Google-owned DoubleClick ad network, Yahoo, or Hotmail to decloak users of the Tor anonymity service.
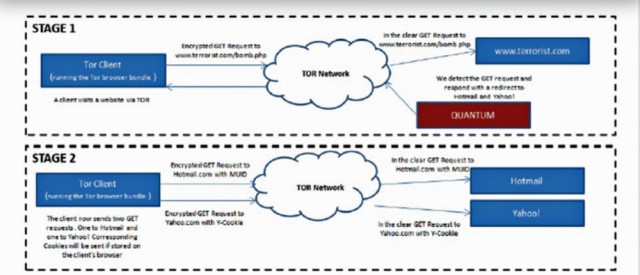
One slide from a June 2012 presentation titled "Tor Stinks" carried the heading "Analytics: Cookie Leakage" followed by the words "DoubleclickID seen on Tor and nonTor IPs." The somewhat cryptic slide led to rampant speculation on Twitter and elsewhere that the NSA and its British counterpart, the Government Communications Headquarters (GCHQ), are able to bypass Tor protections by somehow manipulating the cookies Google uses to track people who have viewed DoubleClick ads. Principal volunteers with the Tor Project believe such a scenario is "plausible," but only in limited cases. Before explaining why, it helps to discuss how such an attack might work.
As documented elsewhere in the "Tor Stinks" presentation, the spy agencies sometimes use secret servers that are located on the Internet backbone to redirect some targets to another set of secret servers that impersonate the websites the targets intended to visit. Given their privileged location, the secret backbone nodes, dubbed "Quantum," are able to respond to the requests faster than the intended server, allowing them to win a "race condition." Government spies can't track cookies within the Tor network, because traffic is encrypted during its circuitous route through three different relays. But if the spies can watch the Internet backbone, they may be able to grab or manipulate cookies once the data exits Tor and heads toward its final destination.
A slide later in the deck refers to something called "QUANTUMCOOKIE," which purportedly "forces clients to divulge stored cookies." There are multiple ways to interpret such a vague bullet point. One of the more plausible is that the Quantum backbone servers can be used to serve cookies not just from DoubleClick or Google, but from Yahoo, Hotmail, or any other widely used Internet service.
Significant constraints
For dissidents of repressive governments, corporate or government whistleblowers, investigative journalists, and other Tor users, the prospect of being outted by a tracking cookie sounds scary. But based on the details included in the slides, it appears there are significant constraints on such attacks.
For one thing, as a separate slide instructed: "Use cookies to identify Tor users when they are not using Tor." Bullet points immediately below read:
"Torbutton" is a reference to a Firefox extension that Tor developers haven't used this way in almost 18 months. The feature allowed users to click a button to choose whether to funnel their traffic through the anonymous Tor network or over their regular Internet connection. By mid 2011, developers warned that the Torbutton could leak cookies or other data from regular Internet connections into Tor traffic, a behavior that could allow eavesdroppers to correlate users' public profiles or viewing history with Tor activities that were presumed private. The Torbutton's "toggle model" was formally purged from the Tor Browser Bundle in May 2012.
The effect of this change, as well as additional improvements that more carefully deleted all cookies when the Tor Browser Bundle is closed, is that the described attacks using cookies from DoubleClick or other services are in most cases not possible.
"The key point here is that it doesn't matter now if you can trick the browser into revealing its cookie anymore," Roger Dingledine, the lead Tor developer who often goes by the handle arma, wrote in an e-mail to Ars. "Back when we used the 'toggle' model, you might have a cookie on your browser that was created when you were in 'not using Tor' mode. That cookie is really dangerous if they can get a hold of it while you're using Tor, because it links you to your 'non-Tor' identity. Now that the toggle model is gone, and Tor Browser is really good about clearing cookies when you close it, then tricking Tor Browser into telling you about its (temporary, session-only, only gotten over Tor) cookies is much less dangerous."
One possible exception that Tor users should be aware of is the risk that comes when they log in to Hotmail, Gmail, or another service, even when running the most recent version of the Tor Browser Bundle. Until users log out and either close the browser or enable the "new identity" function, an attack mounted by a Quantum node might be able to redirect them to an imposter site that's able to retrieve a cookie set by the currently logged-in service.
To recap, here's how a cookie-based attack might work against someone using the old Tor software, based on a scenario offered by Dingledine:
Still a lot work to do
The bottom line is this: there's nothing in the slides that suggests the cookie attacks are a threat to Tor users who run up-to-date software and follow best-practice advice repeatedly offered by Tor volunteers. Of course, it's possible the NSA and GCHQ have techniques. Chief among them is the use of Quantum servers to redirect Tor users to sites that exploit security vulnerabilities to surreptitiously install malware on their computers. Such attacks have long been recognized as a risk, but they come at a cost to spy agencies since success requires the availability of a vulnerability in a current version of the software that can be exploited with no indication to the end user. That requirement makes it harder for agents to carry out the attacks against large numbers of targets.
"Looking over the rest of the slides, they seem to be asking some of the right questions, but they don't seem to have any more answers than we do in the academic research community—and in many cases the papers at http://freehaven.net/anonbib/ provide significantly better answers than these slides do," Dingledine wrote. "Or said more clearly, we still have a lot of work to do to make Tor both safe and usable, but we don't have any new work based on these slides."




0 comments:
Post a Comment